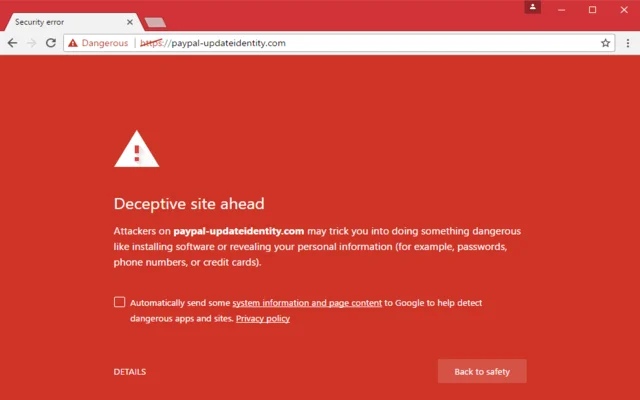
5:53 PM The middle of all phishing websites reflect the lock, making people think that they are actually protected | |
In short: the bulk of non-technical savvy web users hope, in fact, that the lock in the browser bar means, in fact, that the website is considered legitimate and harmless, but it is far from reality. Recent studies show, in fact, that powerful 49 % of all phishing websites have used the protection of Secure Sockets Layer, and, as a consequence, have recommended the lock, as of Q3 2018. According to the latest information from PhishLabs (via Krebs security), 49% of phishing websites with the introduction of SSL increased from 35% in the direction of the last quarter and 25% a year back. The build-up has been put down to the number of phishers who register their own personal domain names and make for their certificates, and yet Chrome displaying "dangerous" on websites that do not have encryption. Certification authorities are not able to figure out any website in order to guarantee its legality, and almost all who request these certificates do not have the slightest content on them at the time. Back in December of last year, according to a sample survey conducted by PhishLabs, in fact, more than 80% of respondents believe that the castle showed that the website or legitimate and non-dangerous, is not correct.
Browser manufacturers resist, working with security firms in order to identify and block fresh phishing websites, but somehow it turns out to Dodge the flag. The safest option is not to include your own data, if you have suspicions on the pretext of the website, including if it has a lock. | |
|
| |
| Total comments: 0 | |